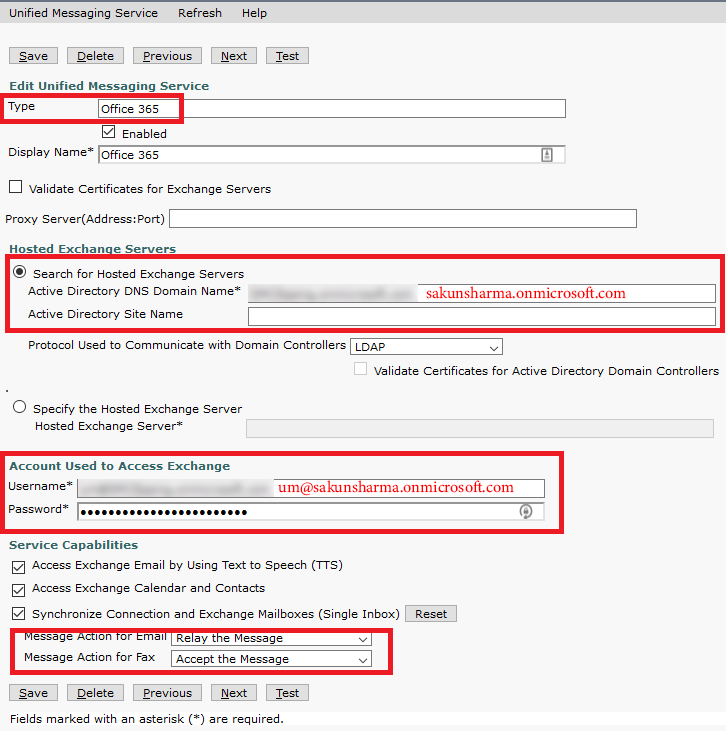
Many organisations are moving user mailboxes from on-premise exchange server to Microsoft Office 365 (O365) cloud service for many reasons. One huddle in moving user
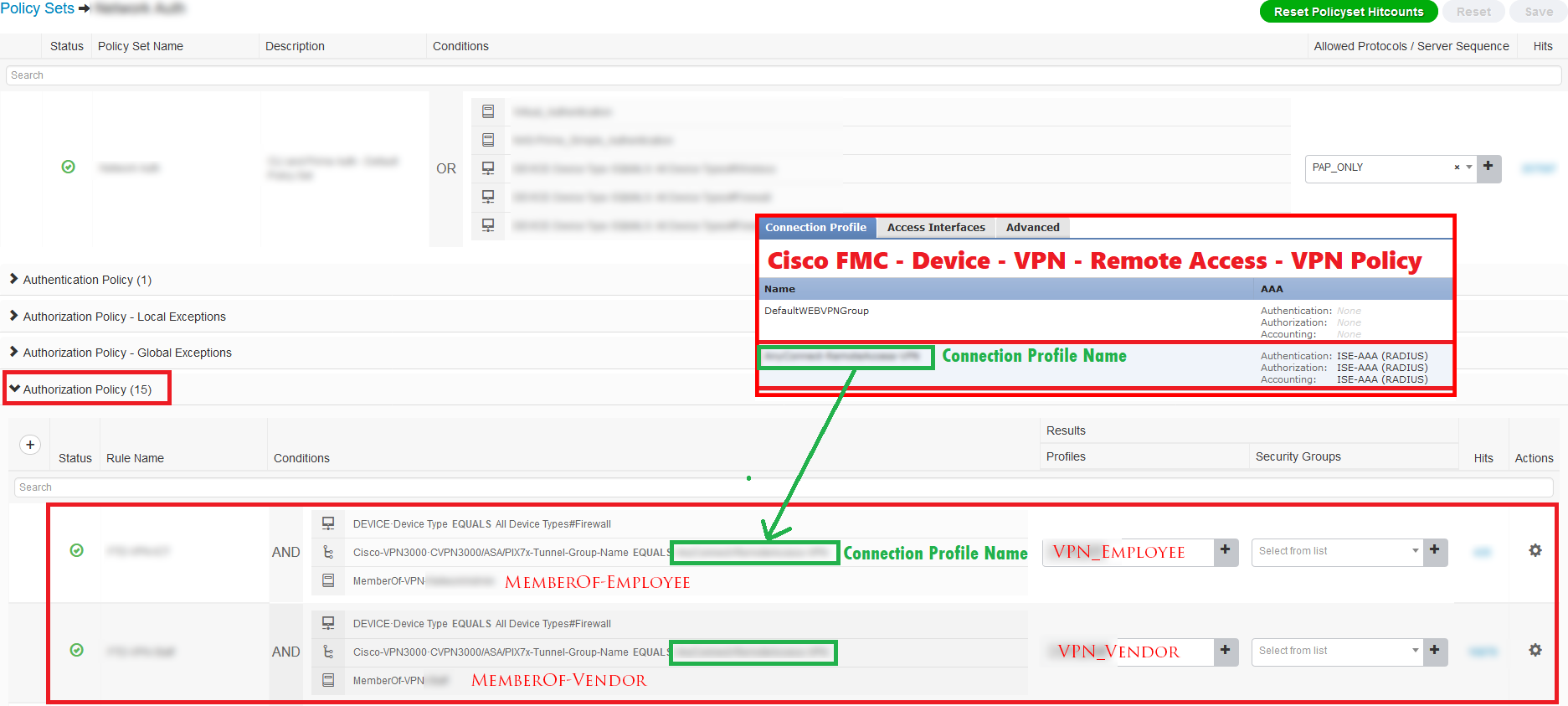
Read MoreDevice Versions in this document: Cisco ISE – Version 2.4 Patch 11 Cisco FMC – Version 6.5.0.4 Cisco FTD – Version 6.5.0.4 In this article
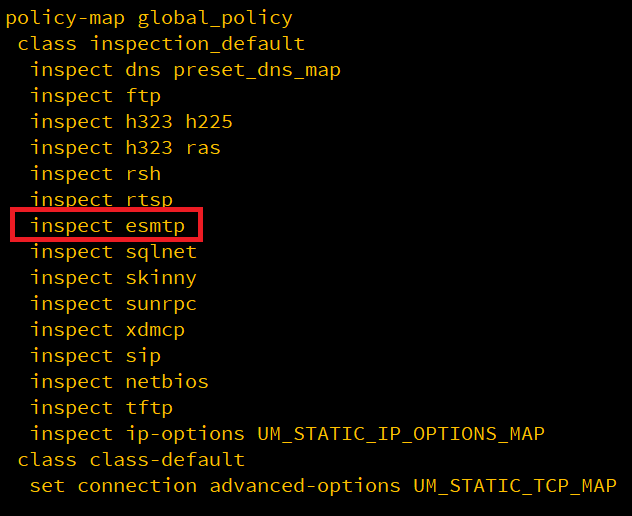
Read MoreWhen ESMTP inspection in enabled on ASA/FTD device and you try to telnet to exchange server, you see rows of Asterisks and cause failure with
Read MoreYouTube Channel Playlist YouTube Channel
Read MoreSSH – Secure Shell is a protocol working with TCP Protocol to provide secured connectivity between two end device. In network we use SSH for
Read MoreSecuring our Router / Switch or any network device is very important. When we talk about security, one is physical security another is securing the
Read MoreARP is a layer 2 protocol, used for obtaining MAC address of any devices within a network. Host machines use ARP protocol to obtain MAC
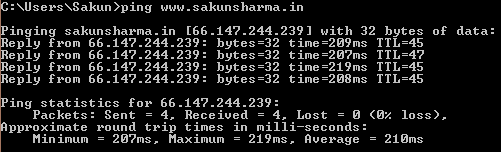
Read MoreDownload PDF Version – Click Here Video Post: There is always a debate on is Ping (ICMP) a layer 3 or layer 4 protocol? If
Read MoreDownload PDF Version Microsoft has introduced virtualization in Windows 8 client operating system for the first time. Yes, Windows 8 support client edition of Microsoft
Read More