Lab: Access List (ACL) in Simple Networks
Download PDF Version
Description:
This lab demonstrates how to use access list (ACL) in simple network to filter traffic. We will use simple access list as well as ip access list in this.
Scenario:
There are two different networks connected through routers. By default router perform the routing between those two networks and working fine. Now company has deployed Client-Server Architecture, and wants to add security so that only particular hosts can access some particular server. Our responsibility is to fulfill the security requirement.
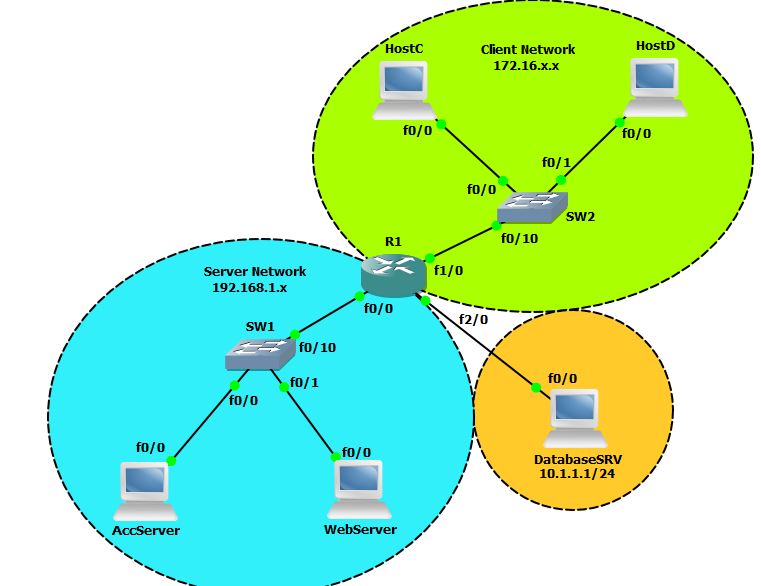
Topology:
Requirement:
- Only HostC can access AccServer.
- Both machines can access WebServer only for HTTP Services.
- Only AccServer can access DatabaseServer.
Device Details:
Implementation:
We will use two ACLs which will be as follows:
- On R1 at s0/1 IN – IP Extended Access list – To allow HostC to access AccServer, allow both hosts to access WebServer and block access to AccServer.
- On R1 f2/0 OUT – Standard Access list – To allow traffic only from AccServer and block rest all.
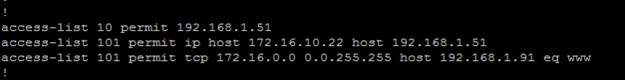
Access Lists:
On R1 at s0/1 in:
Extended IP access list 101
10 permit ip host 172.16.10.22 host 192.168.1.51
20 permit tcp 172.16.0.0 0.0.255.255 host 192.168.1.91 eq www
Command: access-list 101 permit ip host 172.16.10.22 host 192.168.1.51
access-list 101 permit tcp 172.16.0.0 0.0.255.255 host 192.168.1.91 eq www
Here we have created an extended numbered access list 101, which contains two statements with sequence number 10 and 20.
10 : To permit all ip protocols from host 172.16.10.22 to host 192.168.1.51 – This statement will permit traffic from HostC to AccServer.
20 : To permit only TCP Protocol ‘www’ (Port 80) from network 172.16.x.x to host 192.168.1.91 – This statements permit only HTTP traffic from 172.16.x.x network to WebServer.
:: Implicit Deny – At the end of every access list there is Implicit Deny, means packet which does not match any criteria above will be dropped. So that is why all the traffic to AccServer other than from host 172.16.10.22 is dropped and all other protocol traffic to WebServer is dropped.
On R1 at fa2/0 out:
Standard IP access list 10
10 permit 192.168.1.51
Command: access-list 10 permit 192.168.1.51
Here we are creating an Standard Access List to filter traffic to Database Server. In this command at sequence no 10, we are permitting host 192.168.1.51 only, all other will be denied due to implicit deny at the end.
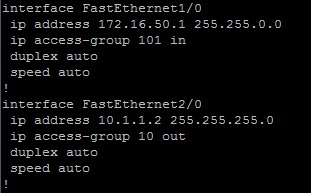
Here we are assigning those access lists onto the interfaces.
Extended Access List 101 is applied at ‘interface FastEthernet1/0’ – ip access-group 101 in. It is configured as inbound access list.
Standard Access List 10 is applied at ‘interface FastEthernet2/0’ – ip access-group 10 out. It is configured as outbound access list.
Testing:
From Host C
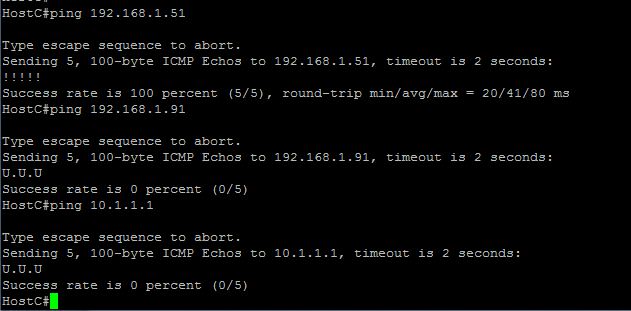
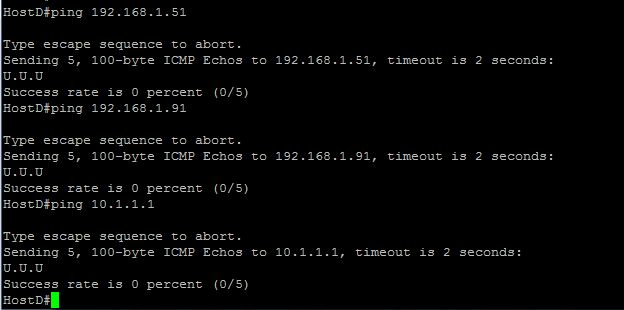
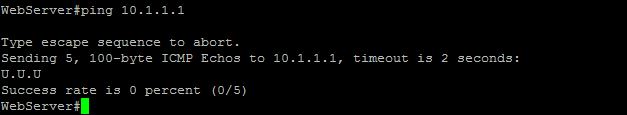
Note: Ping to 192.168.1.91 (WebServer) fails because only HTTP 80, traffic is allowed.
From Host D
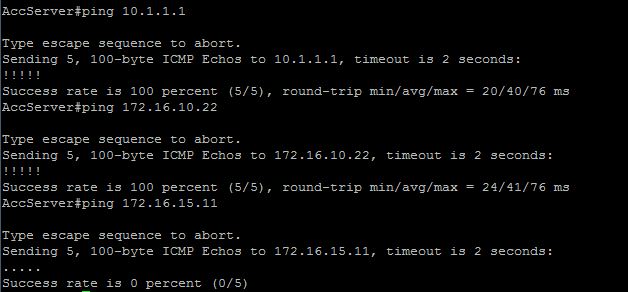
From AccServer
From WebServer
Download GNS 3 Lab:
ACL Simple Lab: https://www.sakunsharma.in/Labs/ACL/ACL_Simple.zip